Why Is the Success of the Insider Threat Program
Why to Pursue a Career in Cyber Threat Intelligence. Leverage threat intelligence to prioritize remediations.

Insider Threat Program What It Is Checklist For Building One Ekran System
Threat Intelligence March 28 2022.

. Threat Intelligence March 9 2022. Complicated threat its many dimensions and the concepts and practices needed to develop an effective insider threat program. Hunting for insider threats or outside attackers Cyber threat hunters can detect threats posed by insiders like an employee or outsiders like a criminal organization.
Partnering for success Connect to one of the industrys largest security focused networks of organizations working together to address todays most critical Identity Security challenges. To mitigate physical and cybersecurity threats it is important to understand the risks posed by insiders and then build a comprehensive insider threat mitigation program that accounts for operational legal. Get breaking Finance news and the latest business articles from AOL.
Integrated threat intelligence URL reputation enrichment separates risky connections from normal ones. There is no way we can give you more information than that without seeing the actual code you are attempting to run. The Cyber Kill Chain.
It revolved around teamwork integrity a spirit of. It might sound surprising to a skeptical public but culture was always a vital part of Goldman Sachss success. Weve helped professionals land jobs at leading organizations.
No matter where you are in your cybersecurity career journey our mission is to equip you with the skills you need to prepare for whats next. Empowering modern enterprises to defend faster at greater scale. Rather it indicates your program is attempting to use all the memory in the system.
Companies should research threats and indicators of compromise most common to their industry and correlate these to corresponding. Cybrary Insider Pro combines expert-led courses with real-world experiences and coaching to drive your success. Proactively hunting for known adversaries A known attacker is one who is listed in threat intelligence services or whose code pattern is on the denylist of known malicious programs.
Threat Intelligence January 1 2022. Netskopes award-winning Evolve Partner Program featuring strong training co-marketing and incentives combined with Netskopes partner-centric go-to-market strategy enables our partners to maximize their growth and profitability while transforming enterprise security. Our data scientists continually introduce new behavior-based threat models to detect evolving tactics techniques and procedures used by APTs.
An Introduction to Qualitative Risk Analysis. Our Singularity XDR Platform encompasses AI-powered prevention detection response and threat hunting across user endpoints containers cloud workloads and IoT devices. The Seven Steps of a Cyberattack.
From stock market news to jobs and real estate it can all be found here. This usually occurs in an out-of-control loop of some kind. The Out of Memory is not based on a limitation in the size a program can be.

What Is An Insider Threat Examples Of Threats And Defenses

Insider Threat Risk Assessment What Is It Why Do You Need It Ekran System
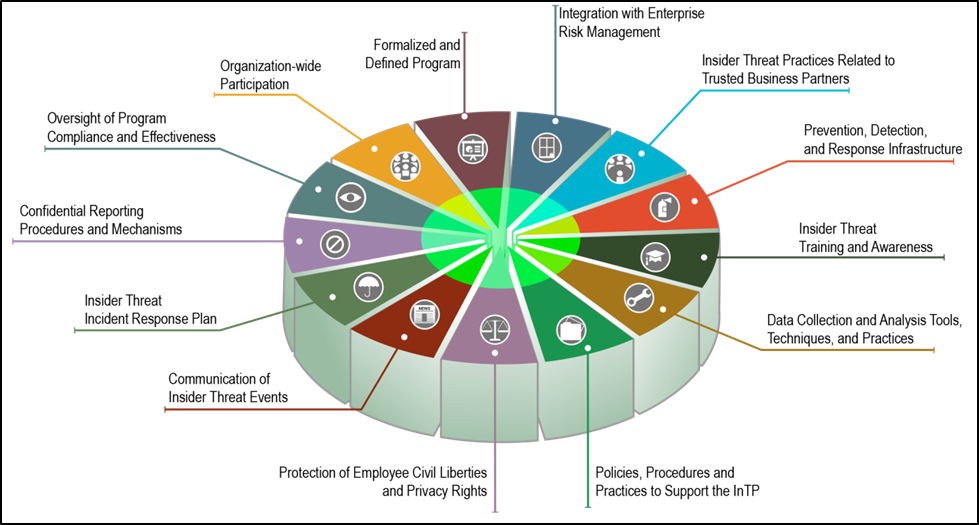
Formalized Insider Threat Program Part 2 Of 20 Cert Best Practices To Mitigate Insider Threats Series

Insider Threat Program What It Is Checklist For Building One Ekran System
No comments for "Why Is the Success of the Insider Threat Program"
Post a Comment